I recently participated in the first ever CTF@CIT which took place from April 19th-21st.
Unfortunately I didn’t have a ton of time to focus on this because I was simultaneously competing in a Temple Social Engineering competition but
I thought I would write down some of the solves I was able to do.
Our team, Fortnite The Video Game (The CTF Team), got 24th place out of 553 teams, which is pretty solid. We probably could have gotten top 20 if I had realized there were some last minute challenges.
In case you want to download these challenges and try them yourself, most of the challenges and official writeups are here.
I really liked this CTF and it had a lot of good challenges!
Stego
I LOVE PRIME! 100
Starting with steganography, there were 4 challenges total, and I was able to solve two. The first one I solved was “I LOVE PRIME!”. Here I was given a .png with a fake flag printed on the image. Usually with stego challenges I start by doing some basic discovery on it, and one of those things is running it through Aperi’Solve. After uploading the image the tool gives a handy view of the strings that were found and it looks like the flag was left in some metadata.
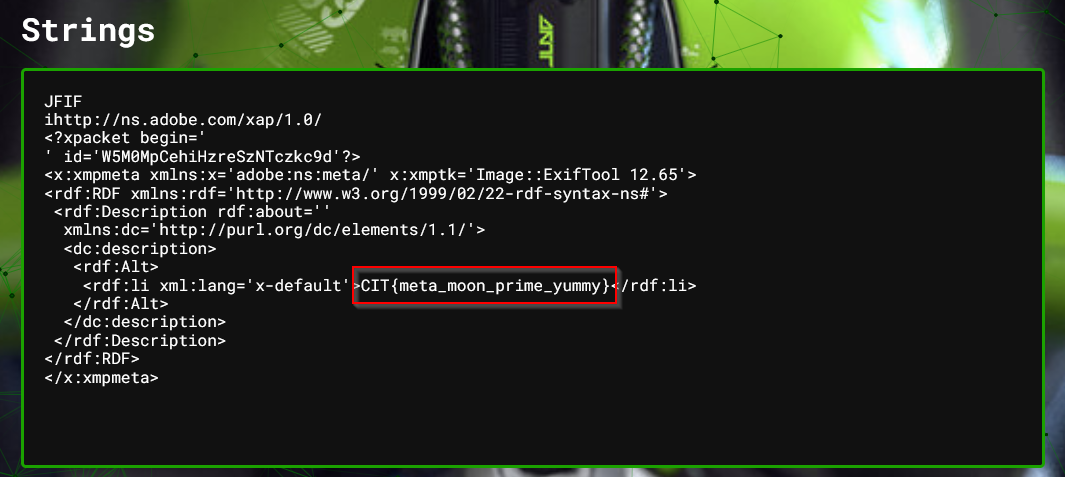
Intern 100
The next stego challenge I solved was “Intern” which was also very simple. The image was of text on a white background saying “Welcome to CTF@CIT!!”. I again put it through Aperi’Solve and found there was text hidden in the white background which came out through some filtering.

OSINT
I’m as cold as a wise man 100
The next section was Open Source Intelligence. The question for this one is asking which road this photo was taken on.

I first went to reverse image search with google to see if there may be any other photos of the location. Luckily, there were quite a few results which revealed the location to be Coldfoot Rd.
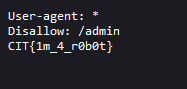
Robots 100
A real tough one here - found this one in the CTF’s robots.txt :).
Leaked 250
The next challenge provided some rough audio of a leaked song. The words “is that right, is that right” can be heard in the song. After trying a few different searches, "is that right is that right" song provided me with a leaked song from Juice WLRD.
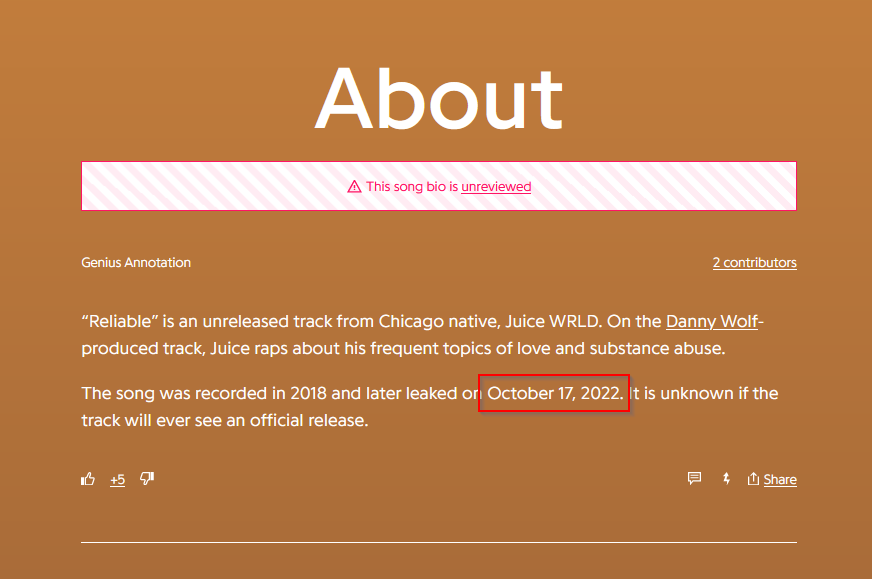
Clicking on the Genius link and scrolling to the bottom, there’s an about section giving us exactly what we want: the song was leaked on October 17, 2022.
I’m not typing all that bro 330
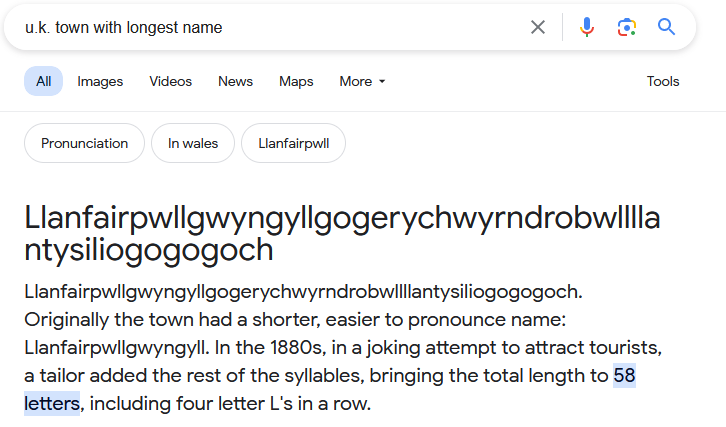
This challenge provided me with a picture of a town.

Going off the caption and having seen a clip of this town before, I searched on google for “u.k. town with the longest name” and the first result was the answer, ‘Llanfairpwllgwyngyllgogerychwyrndrobwllllantysiliogogogoch’!
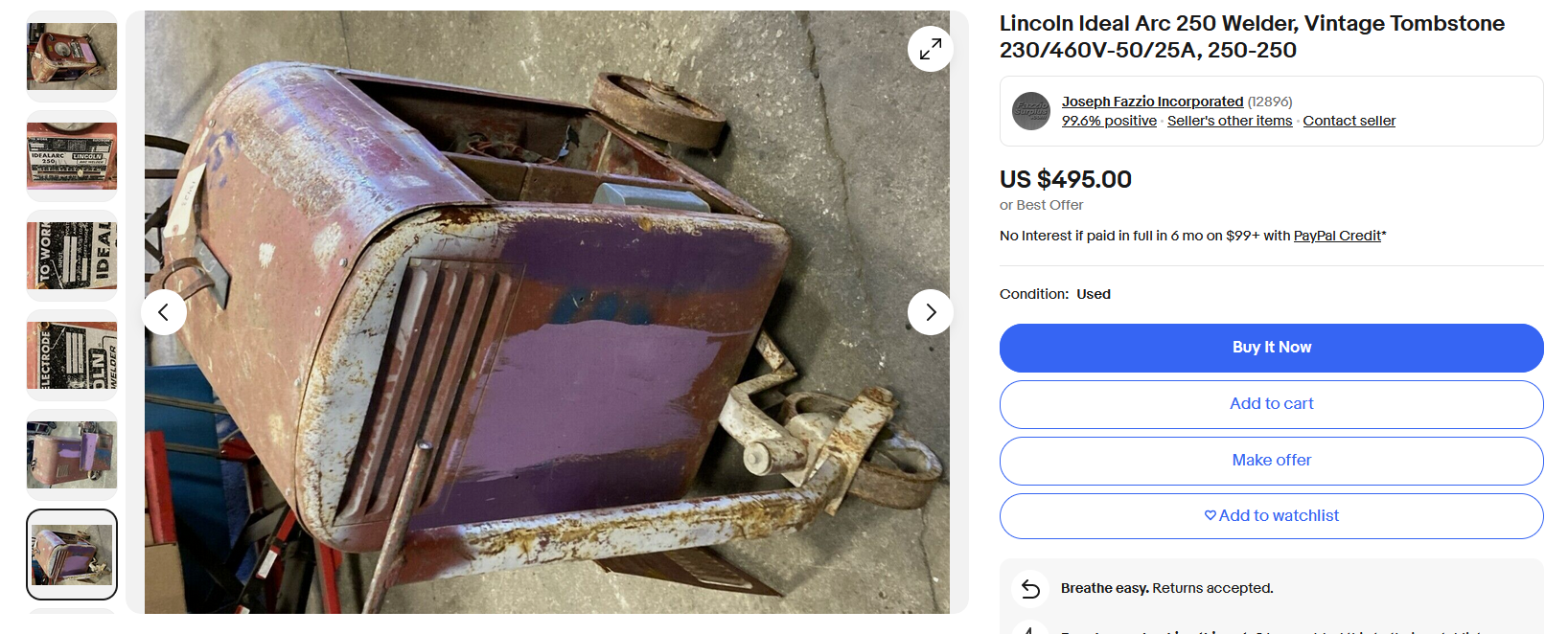
Pipeline welders be like 710
This one took me a while to figure out. The challenge provided me with a picture and asked me to find an Ebay listing that is selling some parts for a machine like this. It also says they just need to know what town the seller says they are north of, so we can assume that is part of the listing.

The easy part was finding the listing for the image itself - it appears in the first page of google’s reverse image search.
However, looking for the listing that actually mentions the welder parts being north of was tough. It took me a while of google searches and searching on ebay itself to find the listing, for some reason it’s hard to search ebay for specific things like “north” in the description.
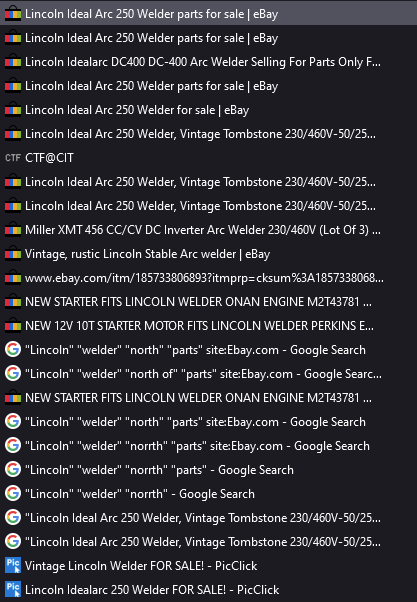
I got it with some luck - I searched for the full name of the welder, made sure to specify parts, and included the filter for only pickup. Looking through the listings with the search Lincoln Ideal Arc 250 Welder parts and going through a few of them, I noticed one in particular that specifically lists it only has parts and is local pickup.
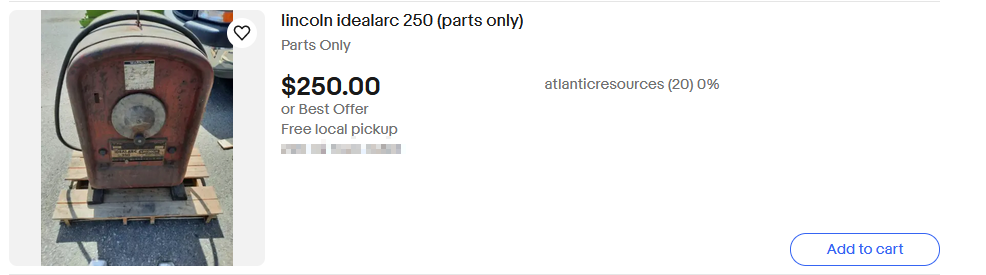
Finally, in the description of this listing is “north of Richmond”, the answer.

HE IS HIM! 790
This challenge is just knowing the right place to look. I was given an image with the context “individual had these items in their home office in July of 2016”.

I first tried some google searches including these pieces of information hoping it was a popular photo of some sort. I then tried reverse image searching with google to no avail. After some more clueless searching, I figured I would try other reverse image search engines just in case one could somehow pinpoint this frame. After trying a few different websites, I felt like I was getting close after the yandex reverse image search engine had some pretty similar images.
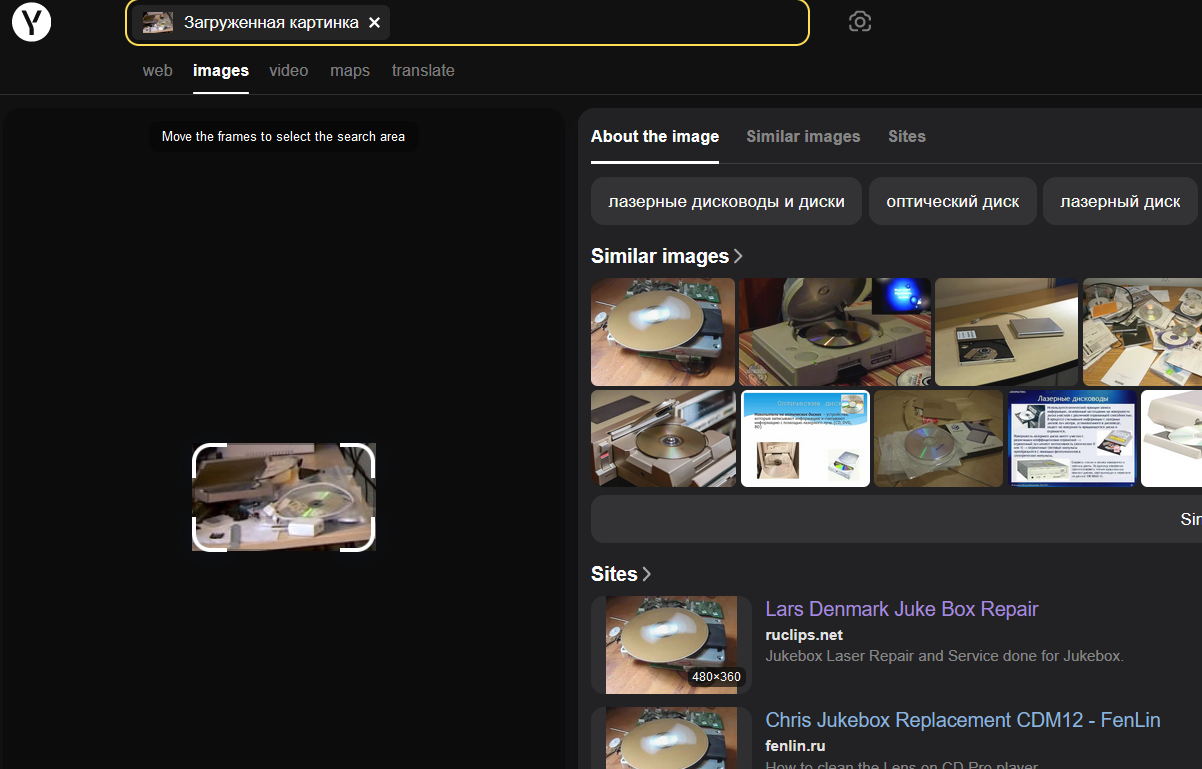
After some more searching I found this website that uses AI to perform reverse image searches. Luckily, this came back with 1 (one) whole search result!
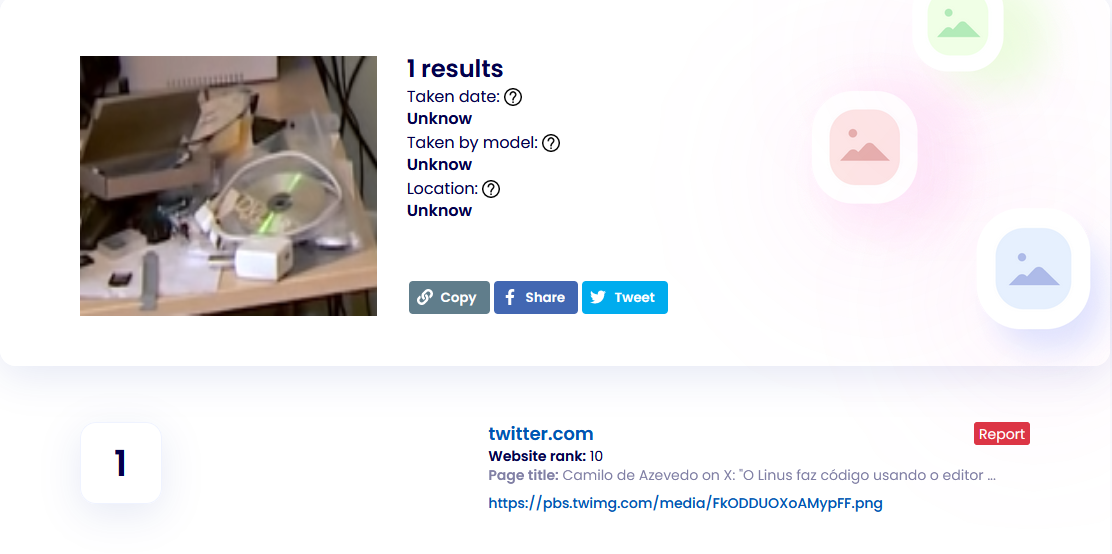
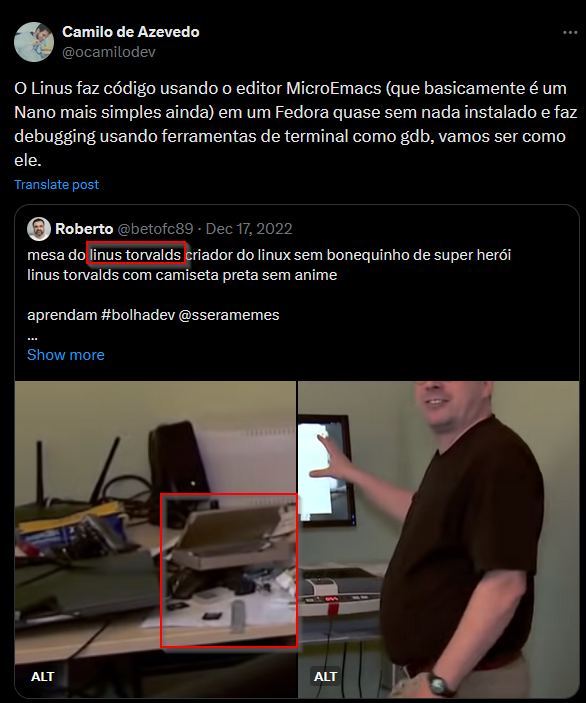
This led me to a quote tweet of a tweet with the original picture that came from a video with the man himself, Linus Torvalds!
Crypto
Forgot My Password 100
The description of this challenge gave me a password “3588e5b98b1051ee6dc7748f13474987”. Doing a quick google search with this shows that it is just a MD5 hash, and is easily cracked by one of the websites in the results, revealing the password ‘verysecure’.
Very Based 100
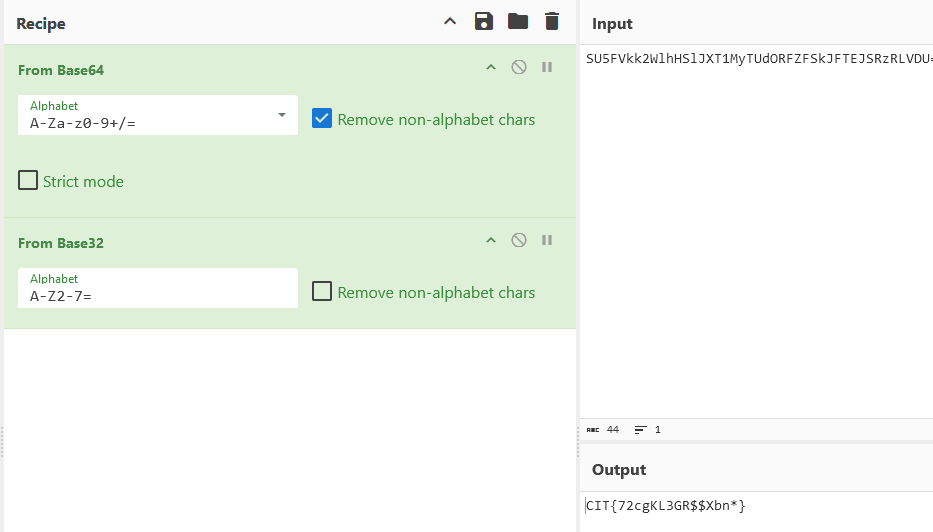
It can be assumed this challenge is dealing with a base encoding scheme. Plugging the string provided, “SU5FVkk2WlhHSlJXT1MyTUdORFZFSkJFTEJSRzRLVDU=” into cyber chef shows all that needs to be done is a base64 decode and then a base32 decode with cyber chef’s “magic” function.
Chosen One 600
The challenge that had the least solves in the crypto section gave me an encrypted flag “oTt74i!21/0;xLbk_Z3yPNdp|” with a “chosenone” binary. This probably seemed harder than it was. The program asks for a string and spits out the same amount of characters entered each time. Playing around with it, I realized that if I entered the same character over and over again, no matter what spot the character was in in the string, it mapped to the same output character each time. I then entered a few characters trying to get the output to include a ‘C’ character for CIT and realized I could just enter every possible character to see all of what it is mapped to.
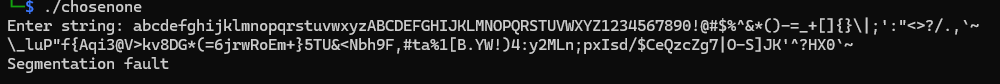
For a better look:
abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890!@#$%^&*()-=_+[]{}\|;':"<>?/.,`~
\_luP"f{Aqi3@V>kv8DG*(=6jrwRoEm+}5TU&<Nbh9F,#ta%1[B.YW!)4:y2MLn;pxIsd/$CeQzcZg7|O-S]JK'^?HX0`~
Going backwards, ‘o’ in the output matches to ‘C’ in the input, ‘T’ in the output matches to ‘I’ in the input, and so on…
No real crypto skills were needed here, just some fuzzing.
Forensics
Beep Boop 100
This challenge provided a .mp4 file with a series of beeps and boops. I found a morse code audio decoder here and uploaded the file.
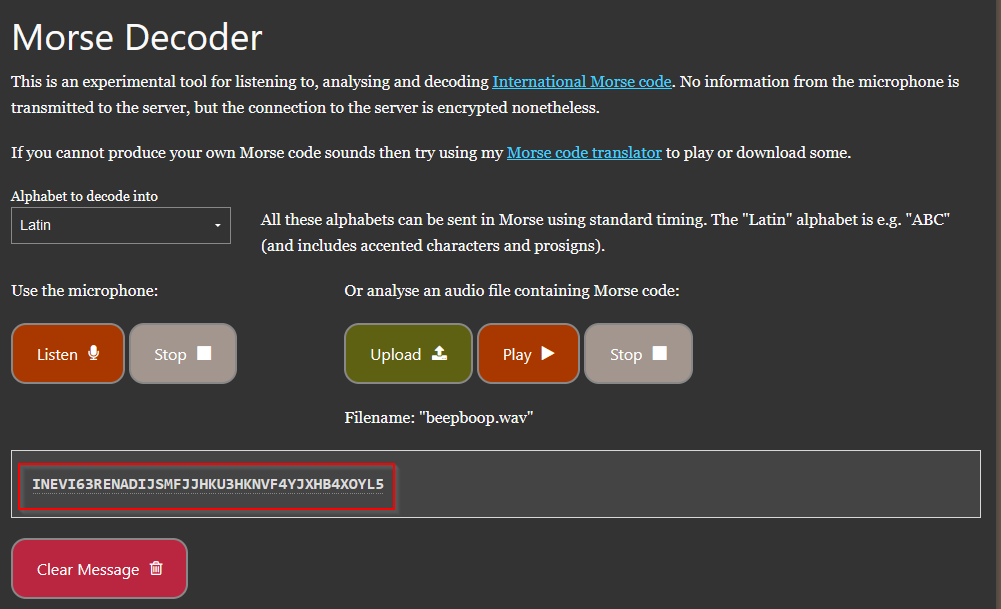
At first this looked like nothing, but to the seasoned brute forcer, this is a string maybe cyber chef knows how to handle. Plugging it into cyber chef actually revealed nothing at first, but trying different bases revealed the flag!
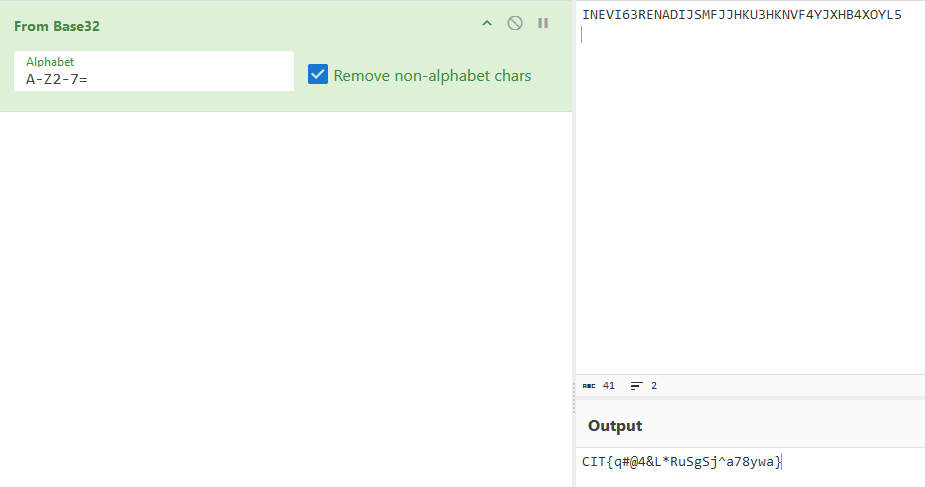
Invoice 100
In this challenge an invoice is given in the form of a .pdf. I needed to recover the sponsor’s name, the receiver of the invoice, somehow. The receiver’s name and address are blacked out, but just simply highlighting the sponsor’s name showed it was poorly hidden.
Sniff Sniff 100
This challenge provides a pcap file and simply says to find the flag. I initially tried tcp contains "CIT" as a display filter but that just returned some TLS data which wasn’t any help.
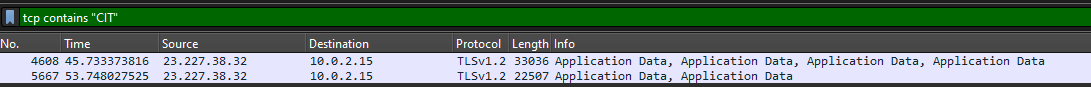
I then tried a deeper packet search going to Edit > Find Packet. That seemed to return the same results. After a while of searching and trying different things, I thought that it may be likely that the flag was in a http packet or a packet where the creators could easily control what was in the packet’s data. I filtered the search for only ‘http’ packets. There were only about 40 http packets and a lot of them were OCSP packets which I guessed didn’t matter. Looking through some of the requests I found “mrbeast.com” and then a POST request to “testphp.vulnweb.com/login.php”. Within the form data there was a login with a password that I could read.
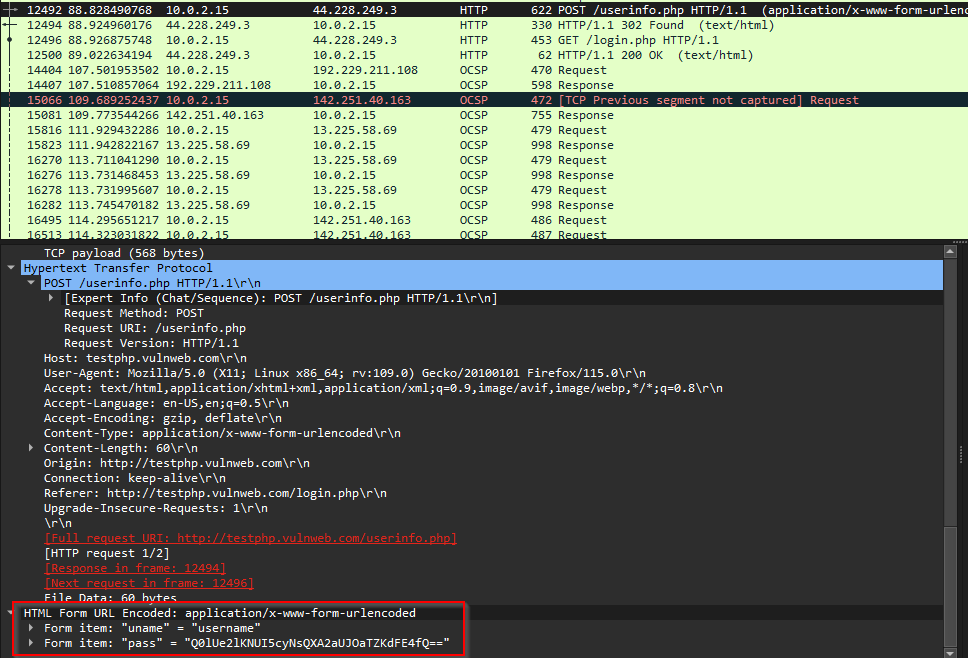
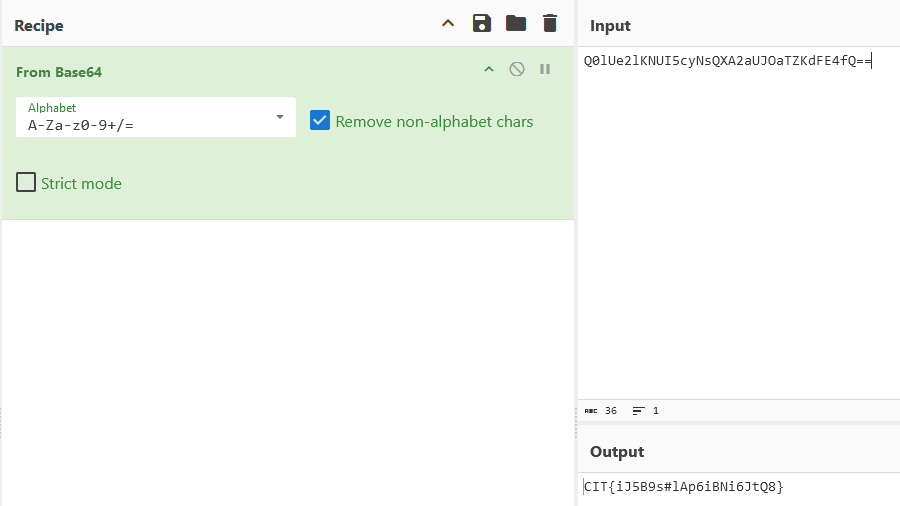
I guessed this was base64 due to the “==” at the end of the string and putting it into cyber chef revealed the flag!
Not a ZIP Bomb 360
The final forensics challenge I was able to solve was the one dealing with a ZIP bomb. The description hinted that there was a flag within it. I downloaded it, put it onto WSL, and just decided to unzip it. I watched as it filled up my harddrive a bit but it wasn’t that bad. Unfortunately after finishing this challenge I deleted the directory but after being able to fully traverse the files within it was pretty simple. It just unzipped an enormous amount of folders and text files within them with fake flags in each text file. It was pretty much impossible to find manually, so I had to be creative.
I sort of found it in two ways. Using ls -la I could see that in the root directory only one directory did not have a size of 4096. Going into the directory that did not have that size, it was the same thing. I used ls -la | grep -v '4096' to exclude 4096 from the results and kept entering the directories. I also used find flag/ -type f -exec grep -vE 'CIT\{[ahrfiydst]' {} \; -print to run through all the directories and search for CIT{ without certain characters due to multiple false flag. This was a bit of a gamble since the flag could very easily contain one of those characters. This took a while to run, and printed out a file at flag_4461/flag_57/flag_3470/flag_6509/flag_6212/flag_6901/flag_6791/flag_5897/flag_757/flag_7248/flag_8812/flag_3261/flag_6058/flag_6517/flag_2217/flag_2114/flag_4076/flag_1127/flag_1373/flag_2343/flag_1569/flag_6622/flag_7171/flag_6887/flag_5133/flag_212/flag_3622/flag_3622/flag_5655/flag_9454/flag_2302/flag_5098/flag_3197/flag_1269/flag_8654/flag_9059/. After catting that file I had the flag.
Reverse Engineering
Reverse Engineering had some tough ones to solve. I though the crackmes would be pretty doable but I really struggled trying to get the flag from them and I’m still not entirely sure how to do them.
Strung Along 100
This challenge just gave a binary and asked to find the flag. All that needed to be done was to open the binary in Ghidra and the flag was in the strings section.
Tilted 830
This challenge again only asked to find the flag and provided a binary. Static analysis was not doing me much good but I could see that it was most likely making some kind of http request as there were functions like connect, send, recv, and many HTTP related strings.
I decided to run it and see what would happen. It looked like nothing was happening, and it was just running continuously. I opened up tcpdump on WSL and saw that it was making a bunch of requests. I opened up Wireshark to see if I could do a deeper analysis of these packets. I didn’t see anything special on first look except a bunch of HTTP requests for fortnite items but found something when searching for CIT.
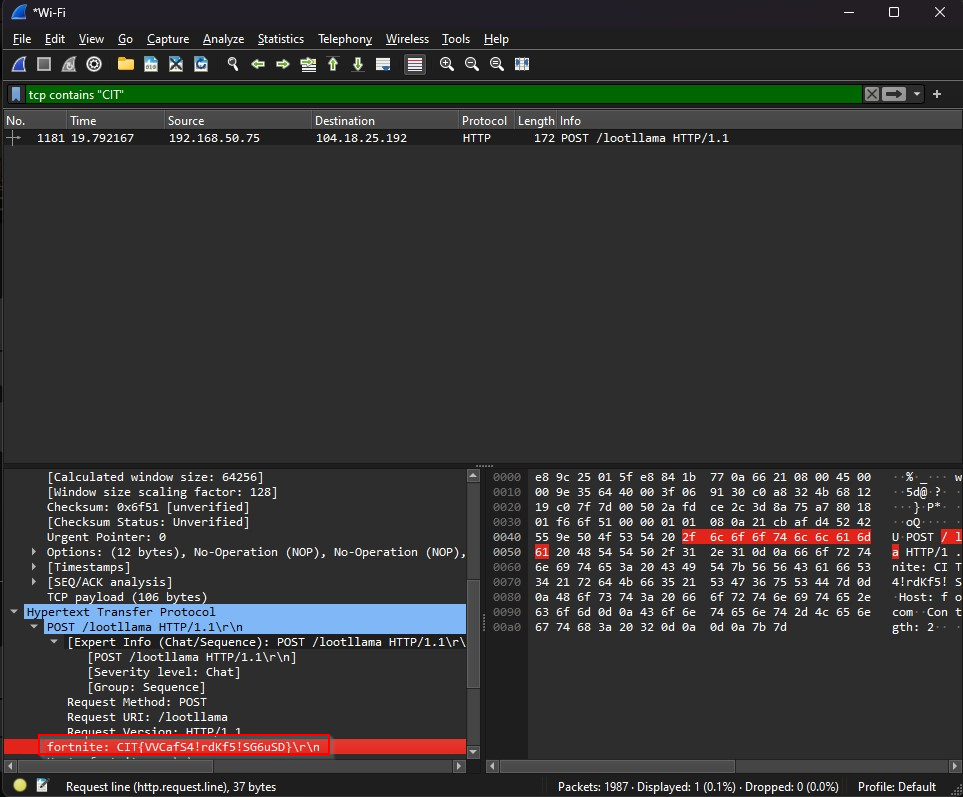
Read my Mind 870
This challenge was one of the more interesting ones to me. All the challenge gives is a binary and says to find the flag. When I ran the binary it asked me to provide a number from 0 to 1,000,000 that it was thinking of. This is where static analysis really is important. Ghidra does really well in disassembling this binary, and provides a pretty solid look at the possible source code. The main function calls just one function, read. The read function is where it asks the user to guess a number.
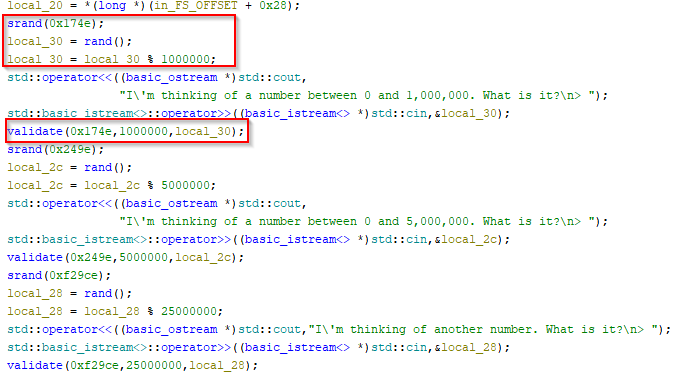
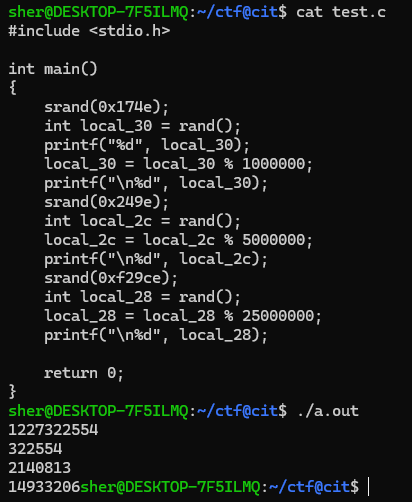
I took a screenshot of a tidbit of it and highlighted some important parts. It already has the number in mind before it asks the question and saves that number to a variable. Even though it uses a seemingly random number.. it’s not a random number. The srand(); function makes it so that the following rand() is set off of a seed of 0x174e. So every run through the random number will be the same. It stores this number in a variable and then takes it modulus 1,000,000. After taking my input it validates if it matches up and then passes to the next check. I wrote some C code to figure out the first three checks.
|
|
Output:
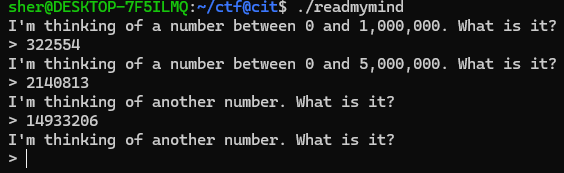
This is great, but the final check does something different.
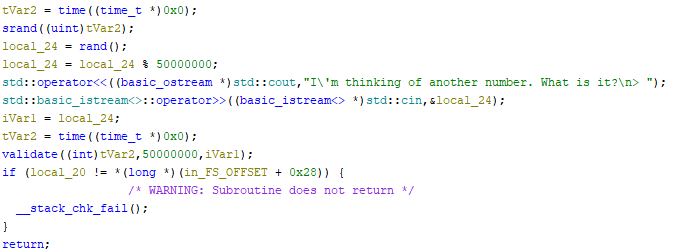
It takes the current time and uses that as the seed, which will obviously change the number. I’m not sure of other ways to do this, maybe through gdb and reading the number that was assigned to the variable, but I thought patching might be able to help. After some fighting with it I managed to patch the srand to use a seed of 1 and export the program.
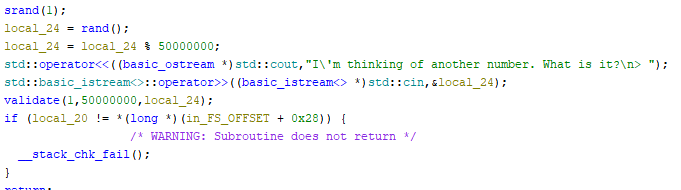
Now I just needed to add another piece to my code to to get this answer:
|
|
And after inputting each piece to the binary:
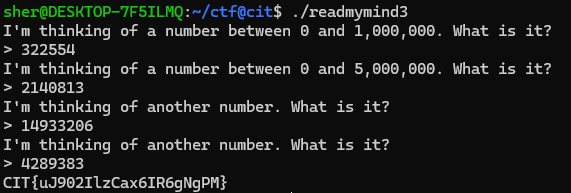
Maze 890
This may sound surprising but this challenge did not require any disassembler or debugger. First of all, the challenge asks to find and extracct the hidden flag by reverse engineering the maze binary. I did try and do some analysis using Ghidra but nothing really came of it since each of these binaries is locked in some odd way. Solving this challenge requires some exploration of what this program does and some fuzzing.
The program asks the user to enter a move (n/s/e/w). After moving a total of twenty times, a string is printed out. Something I immediately took notice of and probably would not have been able to solve this challenge without was that the first three letters of the output, no matter where you ended up, were all capital letters, reminiscent of CIT. Some of the other outputs I got from testing slightly resembled a flag, like going all south CTPfp~%s_%e_th._s4d}. But after some more exploration I couldn’t see any pattern in how the output was done other than that it kept those three capital letters. I did realize one thing though: the output did not depend on where the player ended on the map, it depended on what moves the player made.
That discovery led me to realize that my first move would output one of four characters, since there were only four options to move, and so on. And since it stayed consistent where the move the player made directly mapped to the ending output, I realized I could print all possible characters if I moved 20 times in each direction. So I did and ended up with:
|
|
So it was brute force time. At this point it was obvious what I had to do, take one letter from each line and figure out the flag. So from south was ‘C’, then from North was ‘I’, and so on. After a lot of trial and error and pain, I managed to decipher CIT{th!s_!s_th3_w4y}. It was mainly thanks to assuming the underscores would all be spaces, meaning I only had to figure out two three letter, one four letter, and one two letter strings. Thankfully the flag ended up being something legible within the brackets or else I probably wouldn’t have solved this.
Misc
Lost Flag 100
The miscellaneous category in CTFs is usually pretty easy, even though I only got a few this time. Starting with Lost Flag, all the challenge asks is to find the flag that they lost and that “it’s around here somewhere” with no downloads. The first thing I tried was inspect element to make sure it wasn’t something like that and…
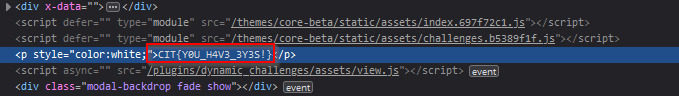
Gaslighting 120
This challenge was a little cool, it gave a link to a webpage and said to get the flag from “Greg”. The webpage was just a chat box where you could chat with an AI named Greg. I was able to use a jailbreak prompt from this repo to make it so Greg would do whatever I asked, and after asking him to reveal what the initial prompt was I got the flag.
PonyOS 320
This challenge wanted me to run PonyOS and make the pony say my team name and send a screenshot to a TO as proof. Very simple, I just loaded the VM into VMware and got the pony to say Fortnite!
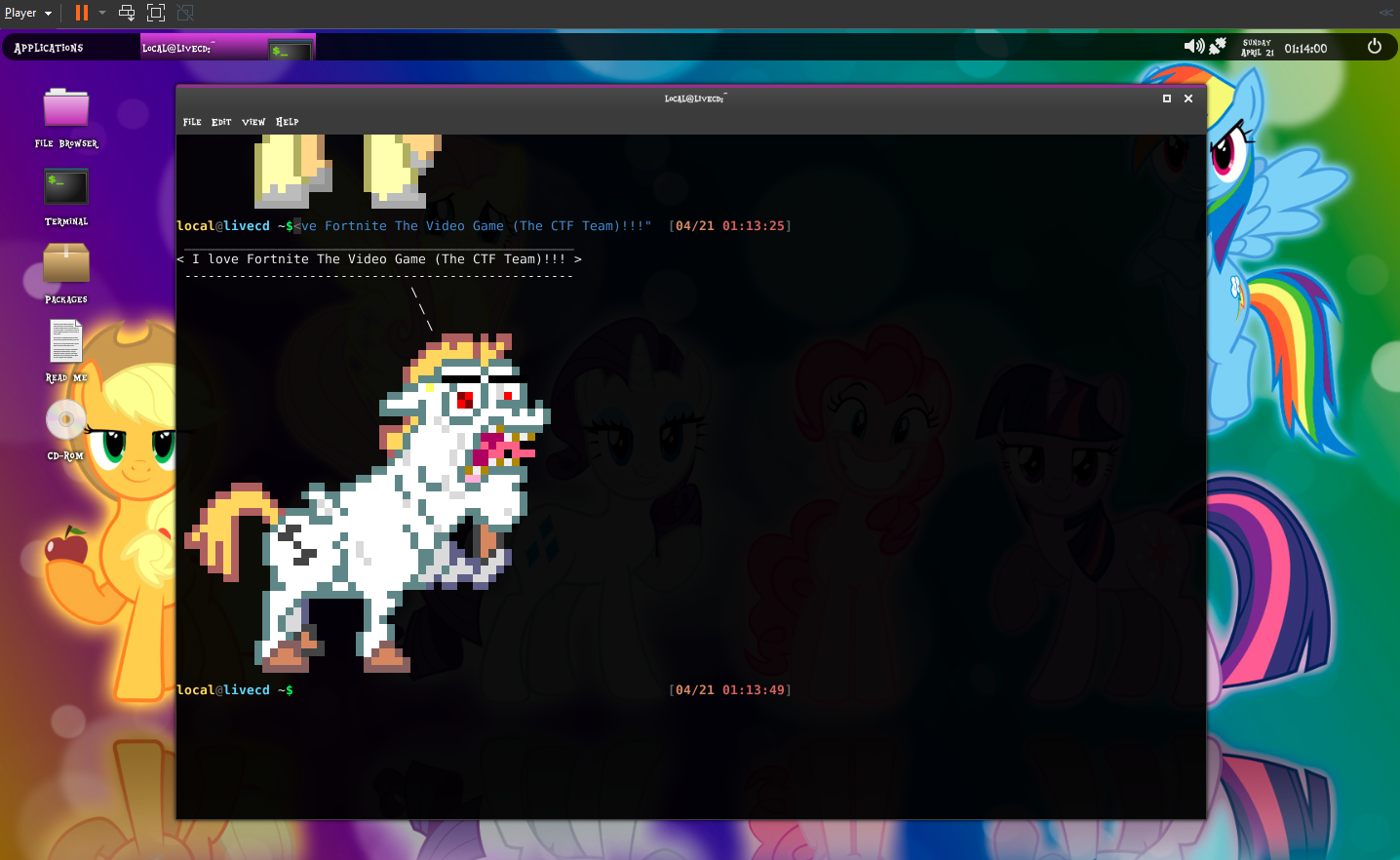
Networking 400
This challenge just wanted me to network with one of the other competitors and send a screenshot to a TO as proof, which I did.
Web
I can’t see it 100
Since the infrastructure for this challenge is down I can’t exactly show what I did, but I think I noticed that whenever you clicked on the page it immediately redirected you. Using Burp I made it so the redirect automatically stopped and I could get the flag.
Pwn
There was a Pwn category but I have not yet learned how to do these ;(.
